Dynamics 365 Security roles are elements which are granted various sets of duties and privileges that give users, assigned to those security roles, access to various “securable objects”, which is just a fancy way of saying menu items, form, reports, inquiries, buttons, and all the other things users interact with throughout the application.
Security roles are meant to contain all the security required for a person in a certain organizational role to complete all their daily tasks and operations. Dynamics 365 Finance and Operations comes with 137 standard security roles. If you are looking for a list of all security roles, duties and privileges please check out my article Security Roles List: All Roles, Duties, and Privileges.
These security roles are pre-built by Microsoft with the security duties and privileges most commonly associated to those roles. Any user assigned to a security role will gain all the access and permissions that come with the role. Users can be assigned to multiple security roles and will receive the sum total access and permission of all assigned security roles.
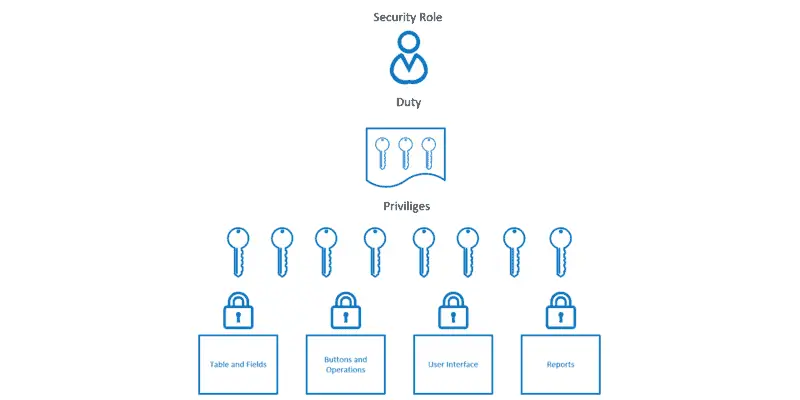
Security roles fall into a hierarchical model with security roles and the top followed by duties, privileges and then the securable objects that are accessed by the security model. Below is an illustration of the Dynamics 365 Finance and Operations security model.
What Is A Duty?
In the security model duties are below security roles and security roles are made up of one or many duties. Duties are a collection of security privileges and typically represent a specific part or piece of a business process. You will see duties like “Maintain customer data”, “Inquire about accounting data”, or “Generate financial reports”. Adding or removing duties is the most common way to grant or revoke access to certain parts of a business process.
Typically, the system administrator will only add or remove privileges when there is a unique or very granular security requirement that must be fulfilled.
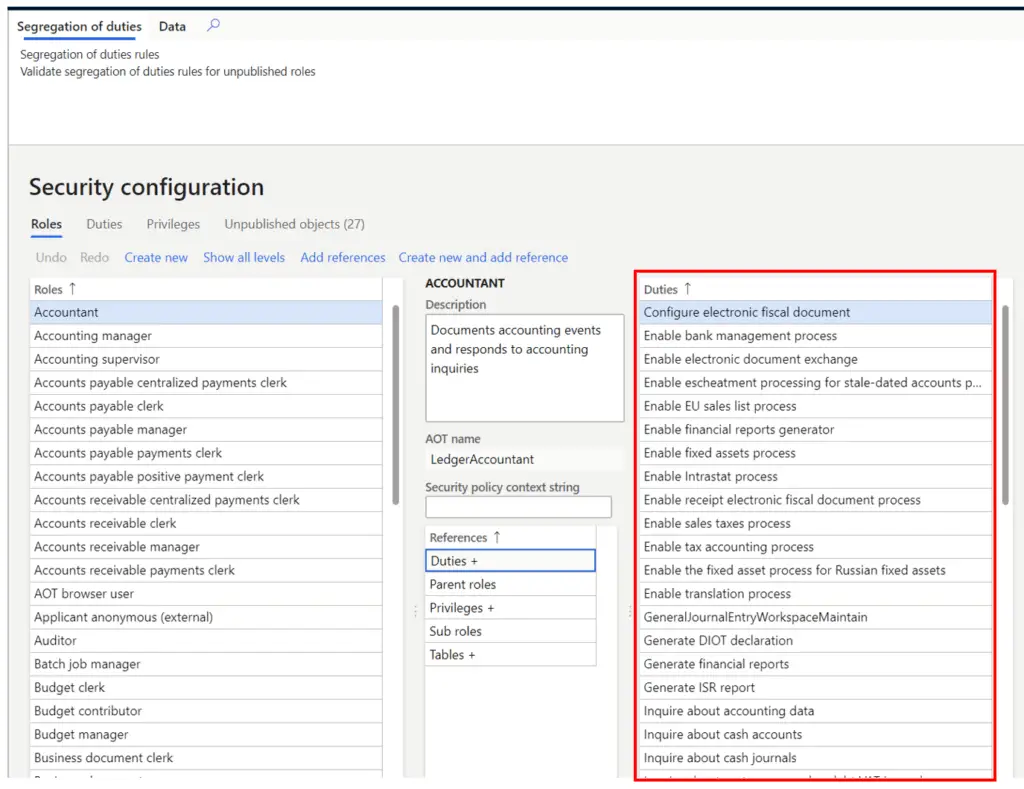
What Is A Privilege?
A security privilege is the lowest level in the Dynamics 365 Finance and Operations security model. The security privilege contains the Create, Read, Update, Delete (CRUD) level permissions that can be toggled to meet very granular security requirements. Although security privileges can be added directly to a security role to meet a specific security requirement, it is best practice to assign it to a duty. Security privileges are the gateway to all access to any securable object in the application.
Create A New Security Role
- To create a new security role, navigate to System administration > Security > Security configuration.
- Click the “Create new” button.
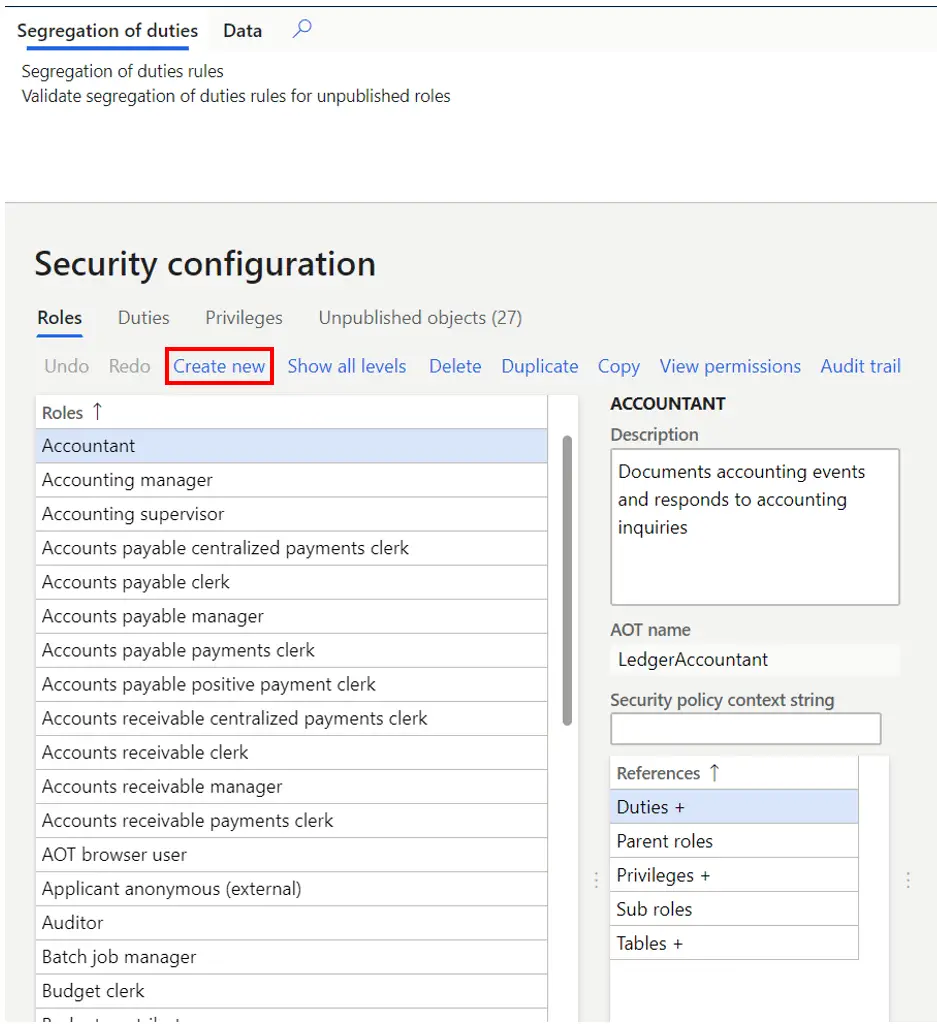
In the “Name” field enter the name of the new security role and click the “Ok” button.

Assign A Duty To A Security Role
Now that we have a security role created, we need to add some duties to the security role.
- To add a duty, find your security role you just created, click on it, and click on the “Duties” reference in the middle of the form.
- Click the “Add references” button.
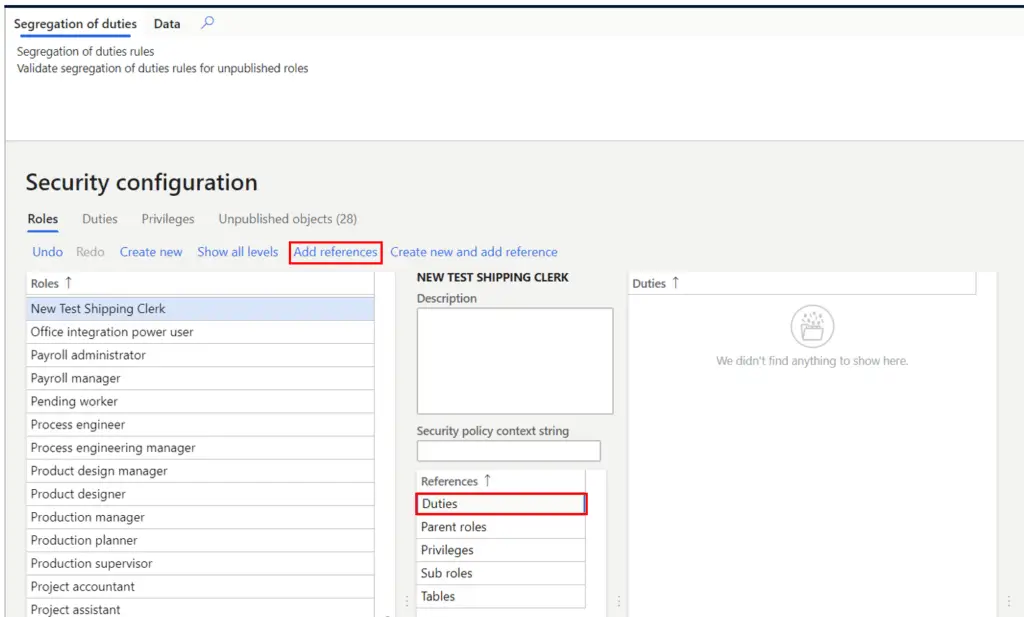
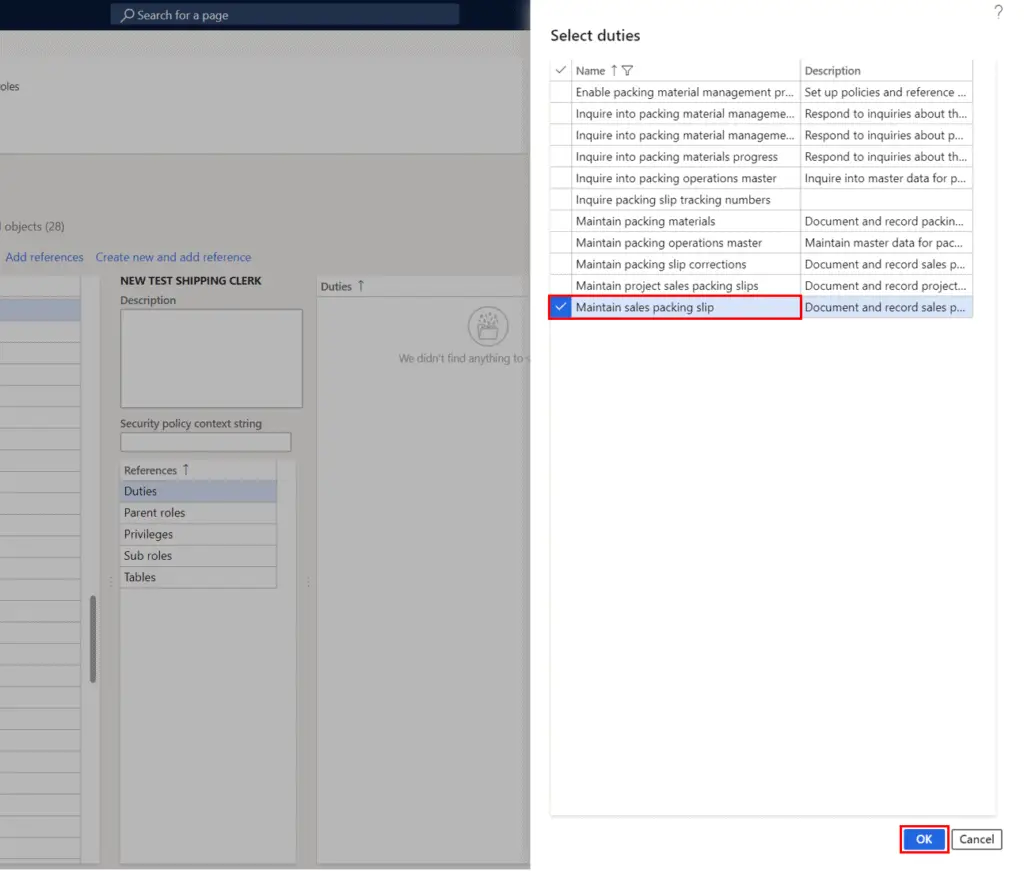
This will open the duty selection pane. Select the duty you want to add and click the “Ok” button.
Assign A Privilege To A Duty
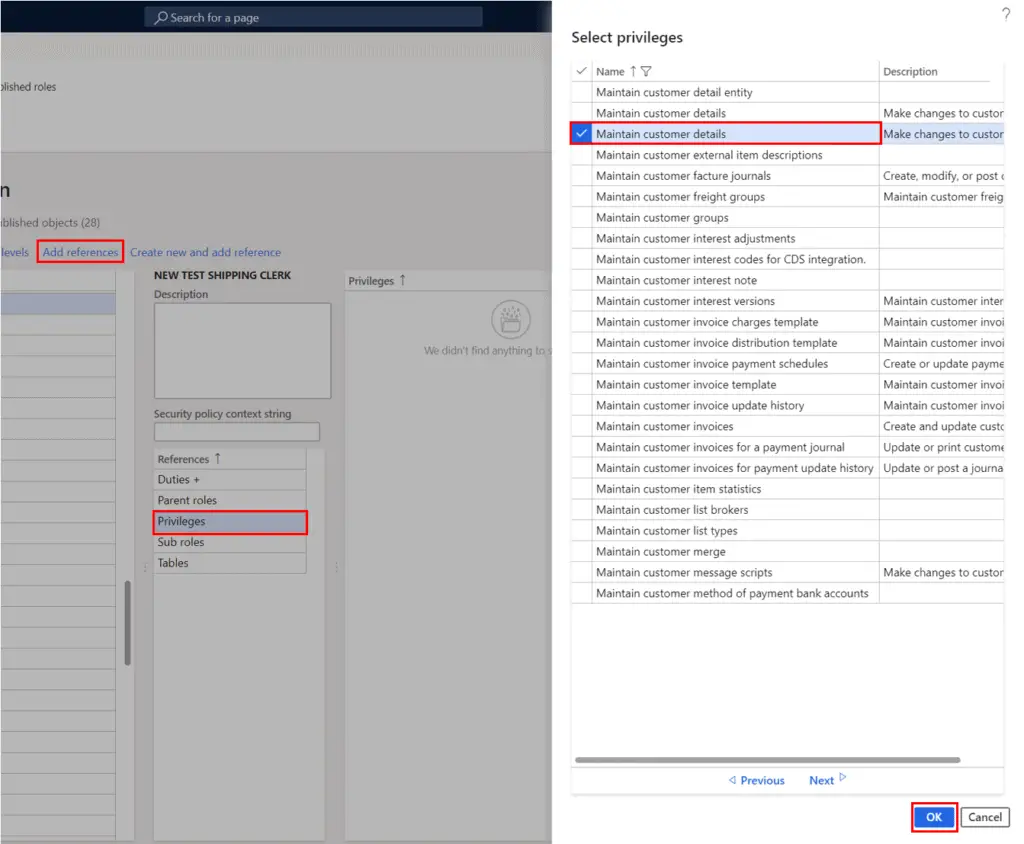
- You can add specific privileges to your duty by clicking the “Privileges” reference in the middle of the form.
- Then click the “Add references” button again to open the privilege pane.
- Select the privilege that you want to add and click the “Ok” button.
If you’re asking, “how do I know which duties or privileges I need to assign?” There are many ways, but I would recommend two approaches.
The user interface in Dynamics 365 Finance and Operations does not provide a very good way to search for the privileges you need and what privileges are assigned to what duties all in one view. So I would recommend extracting all the roles, duties, and privileges to Excel and just search the excel sheet for the duties and privileges you need. If you need an extract, I have provided one in my article Security Roles List: All Roles, Duties, and Privileges.
Use the Security Diagnostic for Task Recording feature to determine which security roles, duties, and privileges pertain to the business process you are performing. Later in the article I will go through how to use this tool.
Publish Objects
Now that we have created the security role, assigned a duty, and assigned privileges to the duty. We are not quite ready to assign that security role to the user. First, we need to publish our new security role.
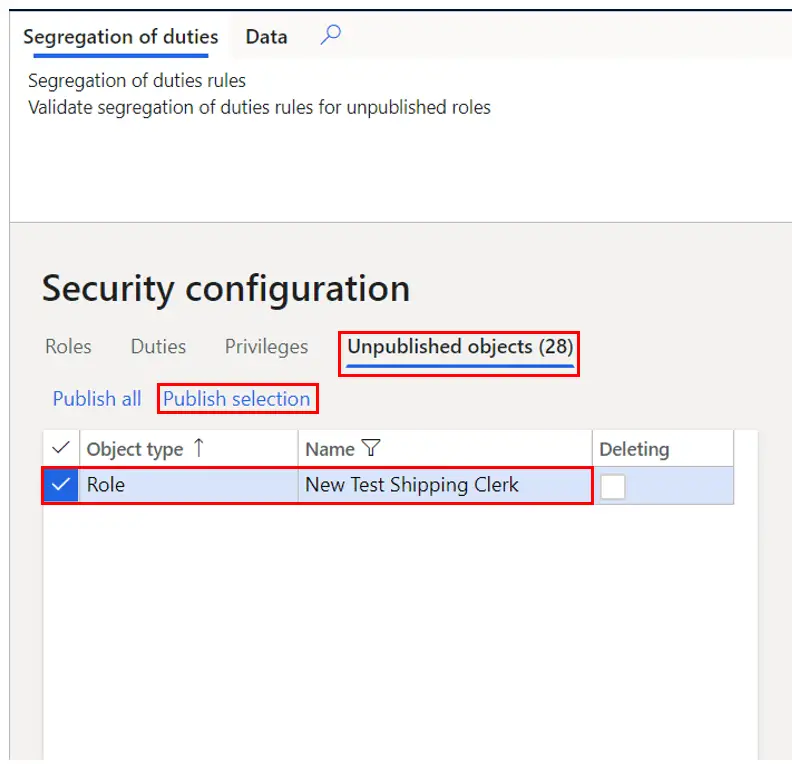
- To publish our security role, click the “Unpublished objects” tab.
- Find the security role we created, select it, and click the “Publish selection”.
Now it will show up as available to be assigned to a user.
Assign A Security Role To A User
In this example we will use the new security role we just created to assign to a user, but you can assign any existing security role the same way.
- To assign a security role navigate to System administration > Security > Assign users to roles.
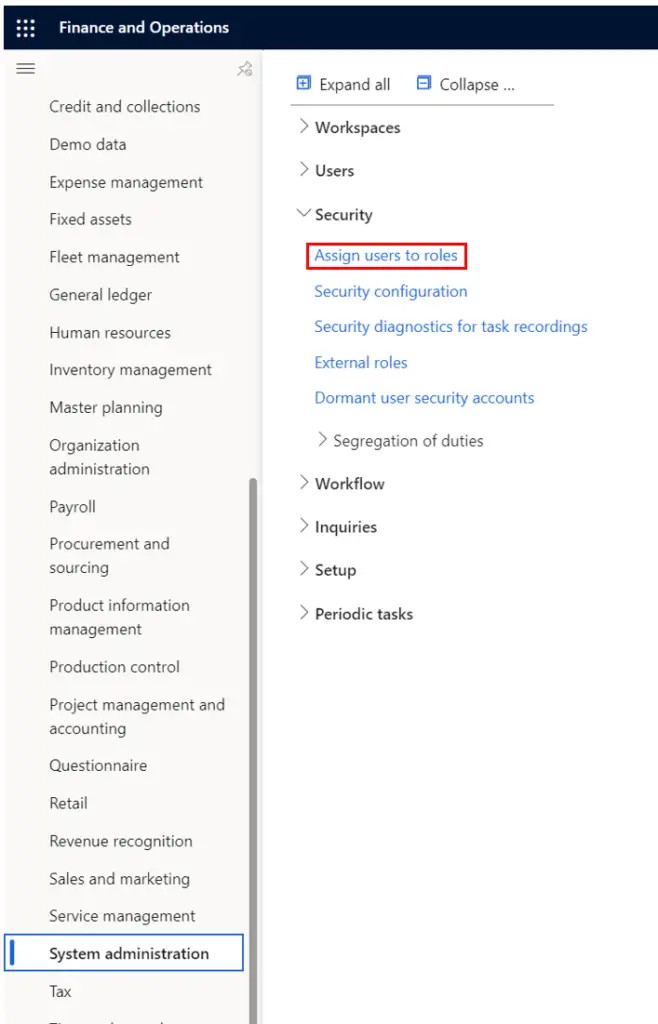
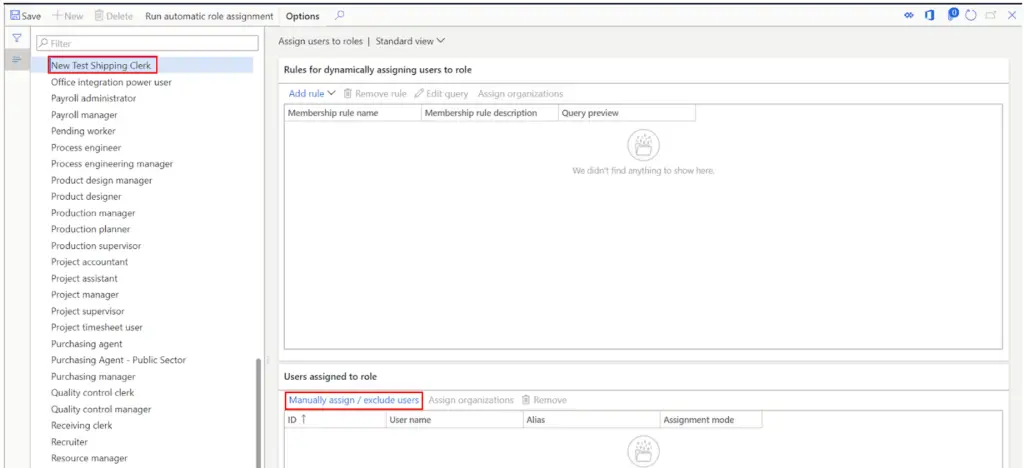
- In the security role assignment form find the security role we just created and click on it.
- Click the “Manually assign / exclude users” button.
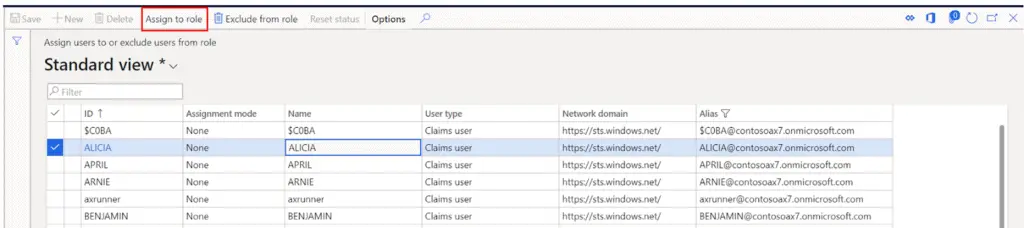
This will open a user selection form. Here you can click on the user you want to associate with the security role and click the “Assign to role button”.
In certain cases, you may want to limit users to certain legal entities. In this example I want to limit this users to only have security access to the “USMF” company.
- To do this click the “Assign organizations” button.
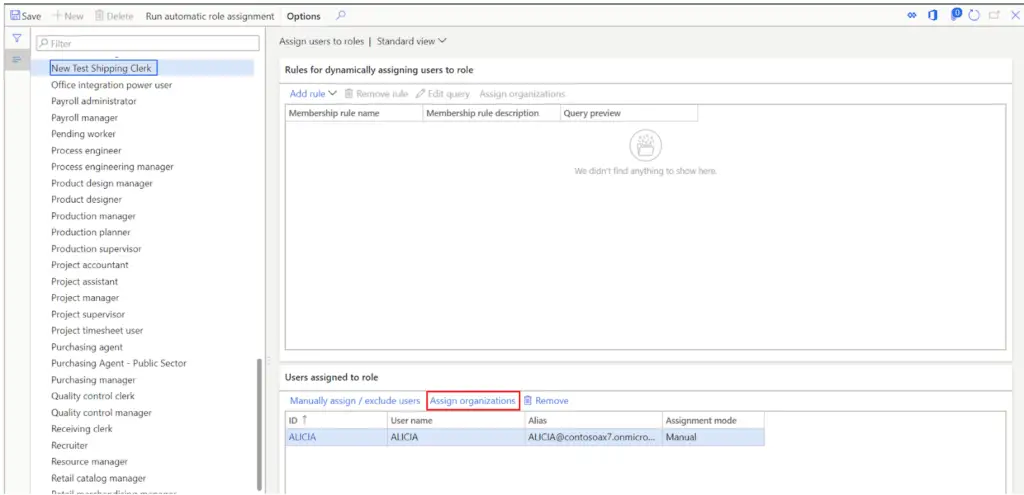
- Click the “Grant access to specific organizations” option.
- Click the legal entity you want to grant access to and scroll down to the bottom of the page.
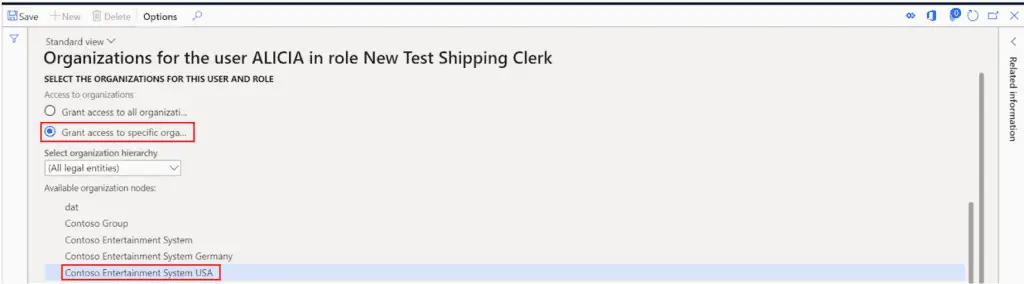
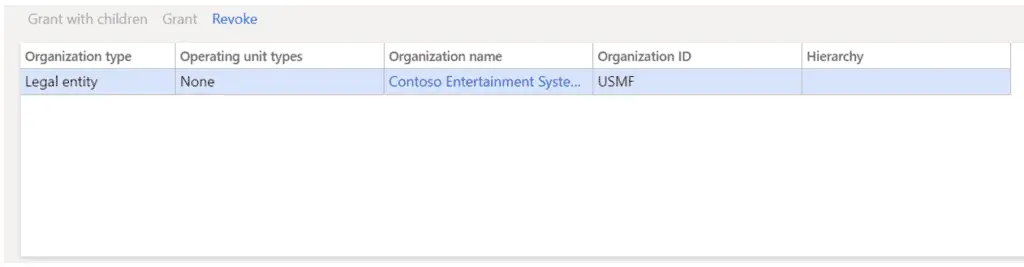
Click the “Grant” button and you will see the legal entity you selected brought into the grid.
Dynamically Assign Users To Security Roles
There are some cases where you may have a large number of users and it may be a very tedious task to manually assign security roles to users. In the security role assignment form, there is an option to dynamically assign users to roles. This option allows you to build a query associated to the security role that will look for users to assign based on user defined filter criteria. This can offload much of the heavy lifting involved with assigning security roles to users.
- To use the automatic role assignment, click the “Add rule” button.
- In the drop down select the query that looks most relevant. In this example I am going to use the query that is based on user data.
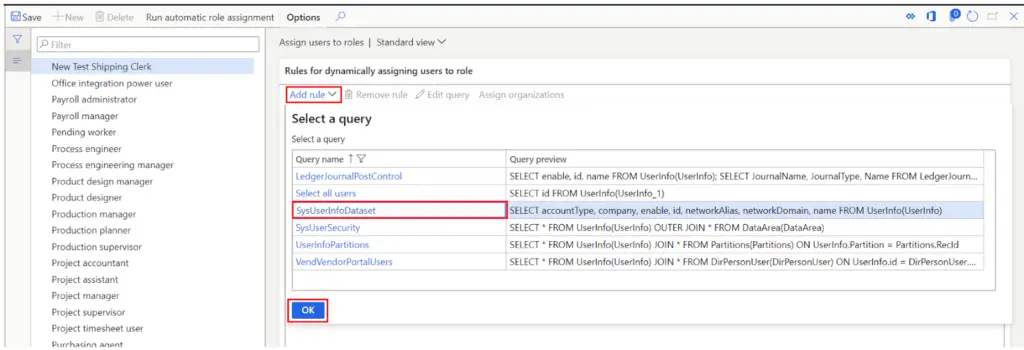
Now that I have selected my query, I can define that query parameters by clicking the “Edit query” button.
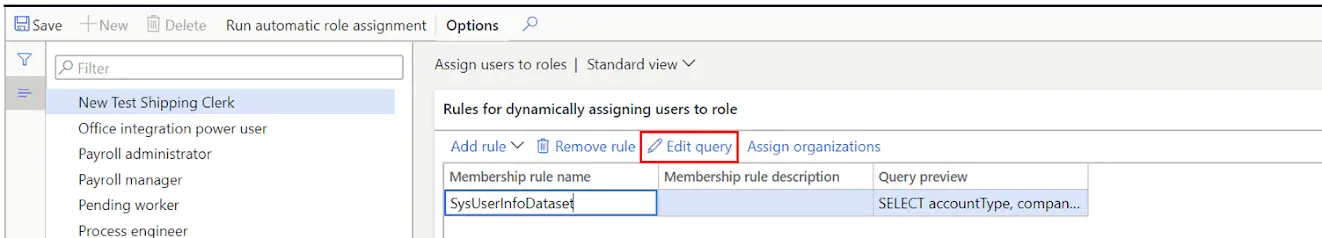
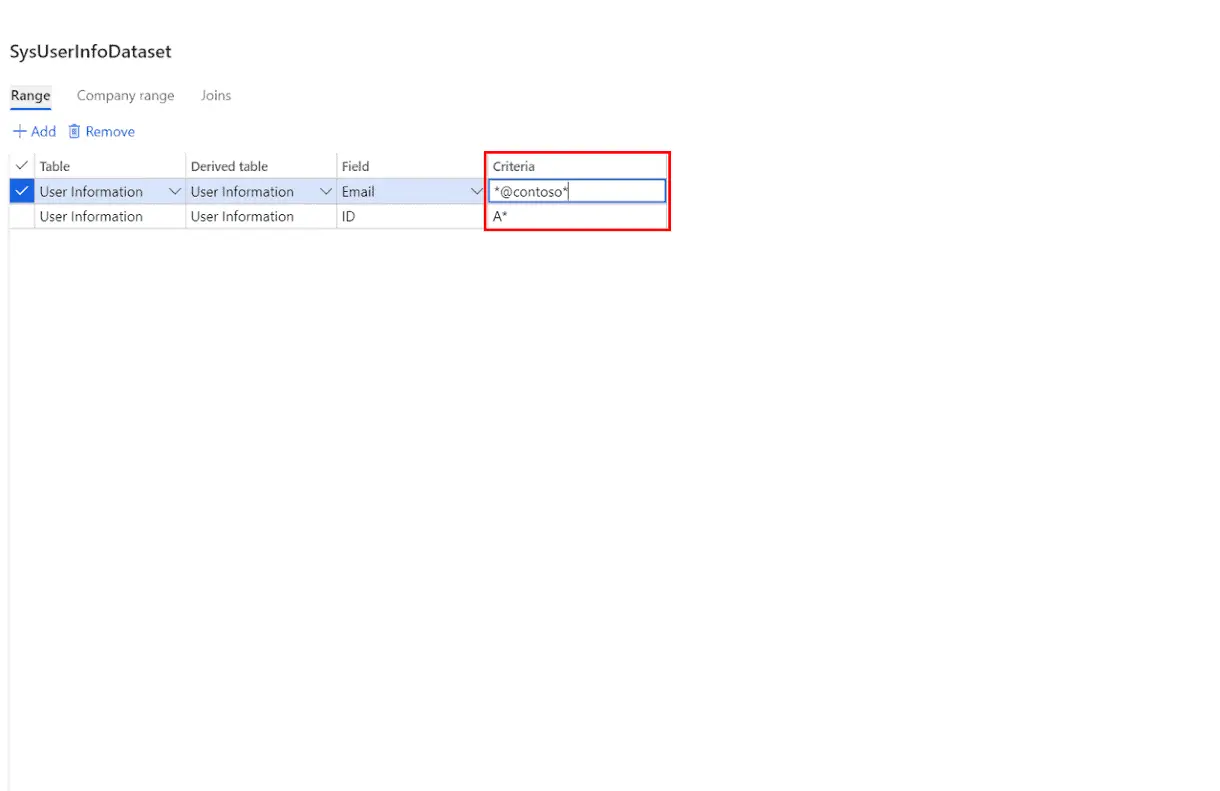
This will open query form. Here I can define that I want to assign this role to all users with a user ID that starts with the letter “A” and has an email that contains “@contoso”.
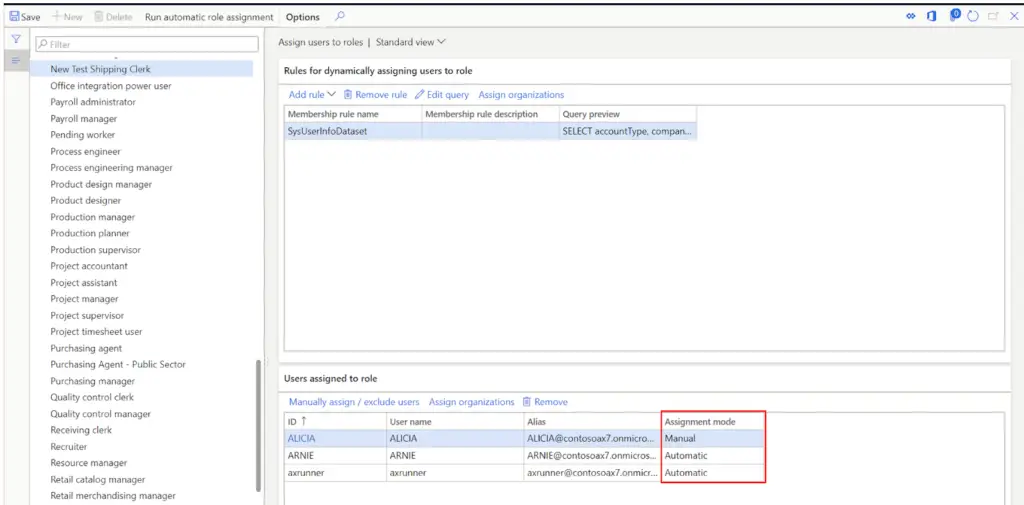
To run the automatic security role assignment based on the query click the “Run automatic role assignment” button.
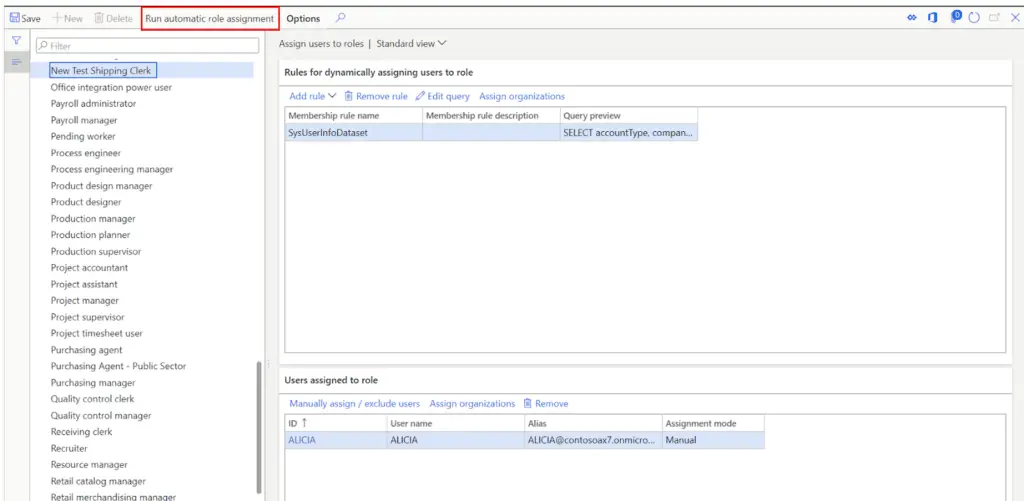
Down in the “Users assigned to role” section, you will see all the users that met the query parameters and were automatically assigned to the security role. You can identify the automatic assignment by looking at the “Assignment mode” field. Automatically assigned users will be set to “Automatic” and manually assigned users will be set to “Manual”.
Security Diagnostic For Task Recordings
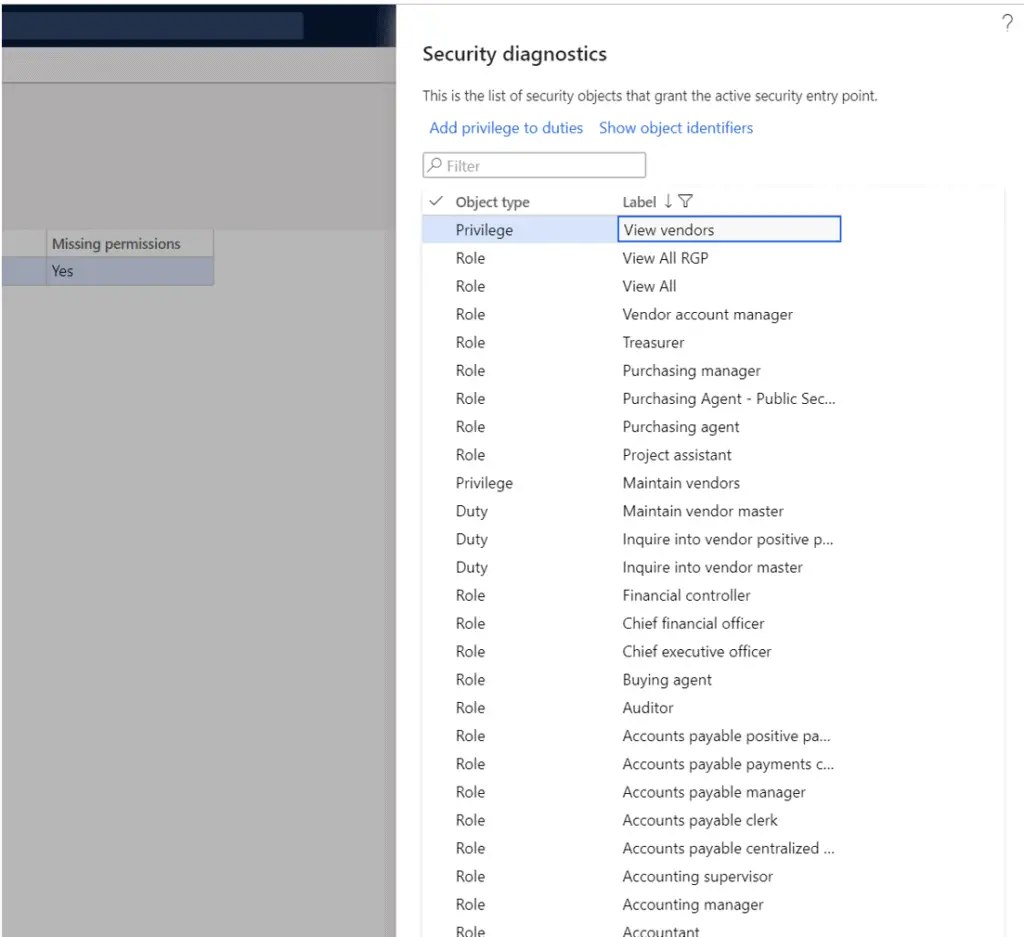
The security diagnostic tool for task recordings is a powerful tool to help security administrators figure out which security roles, duties, or privileges are required to complete a business process. The security diagnostic tool works by analyzing a task recording file to determine if security permissions are missing for a given user and then displays a list of security objects that would grant the necessary permissions to complete the business process.
For this example, I have already created a task recording of creating a vendor record.
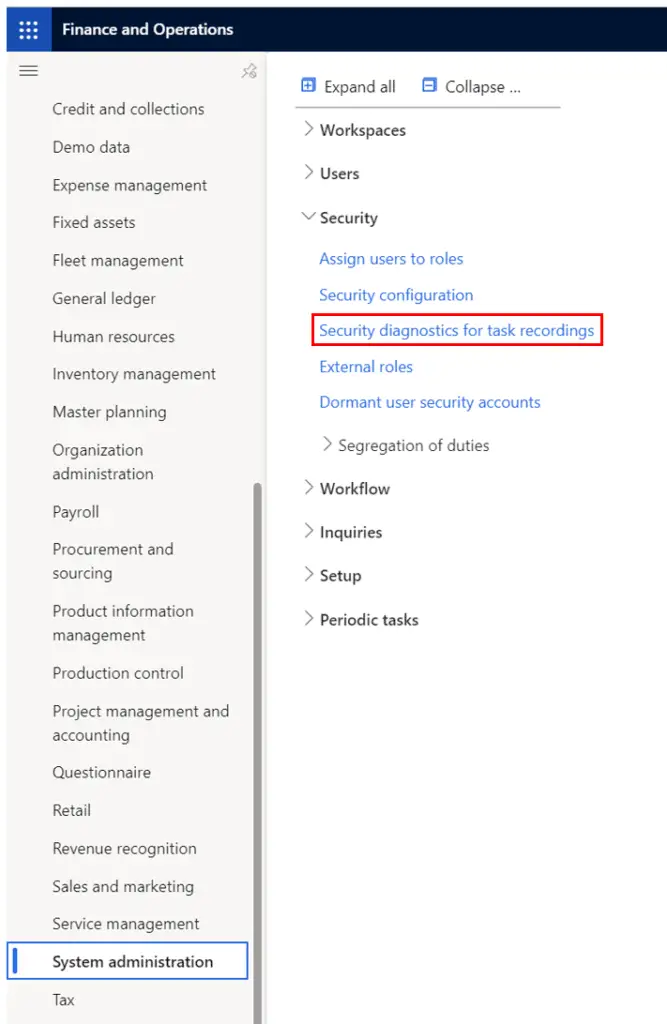
- To use the security diagnostic tool for task recordings, navigate to System administration > Security > Security Diagnostic for Task Recordings.
Click the “Open form this PC” button.
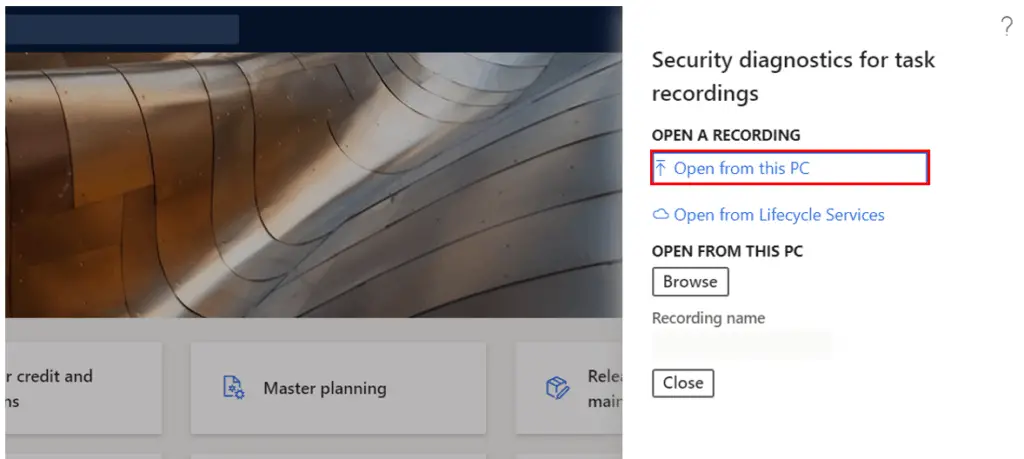
- This will open the file chooser on your computer where you can select a task recorder .axtr file. Click “Close”.
- In the “User ID” field select the user ID where you needing to verify their security permissions to the task recorded on the task recorder.
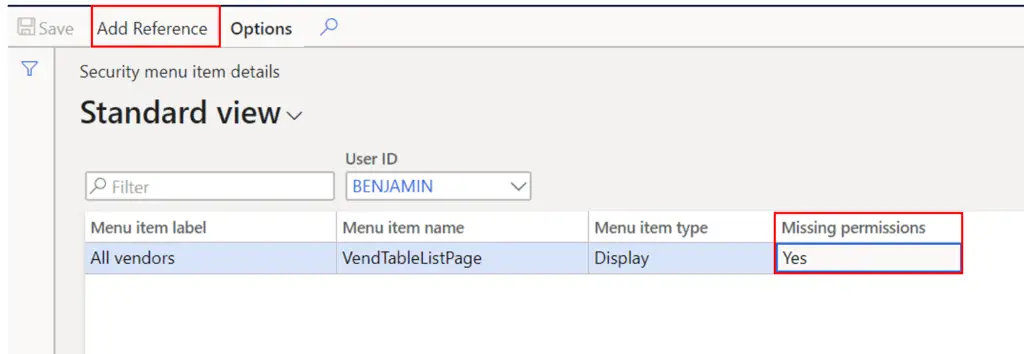
- In the “Missing permissions” field you will see a “Yes” if the user is missing permissions to parts of the task.
- Click the “Add reference” button. This will show you a list of security roles, duties, and privileges that have the required permissions. From here you can add the security role, duty, or privilege to the user.
Takeaways
Security is an extremely important and often overlooked aspect to ERP implementations which leads to problems later in the project. Starting security early and getting security roles assigned and tested is key to a successful implementation.
The security framework in Dynamics 365 Finance and Operations is very flexible and although intimidating at first is very easy to use after you get the hang of it. I hoe this article has shown you some of the basics to managing security and security roles.